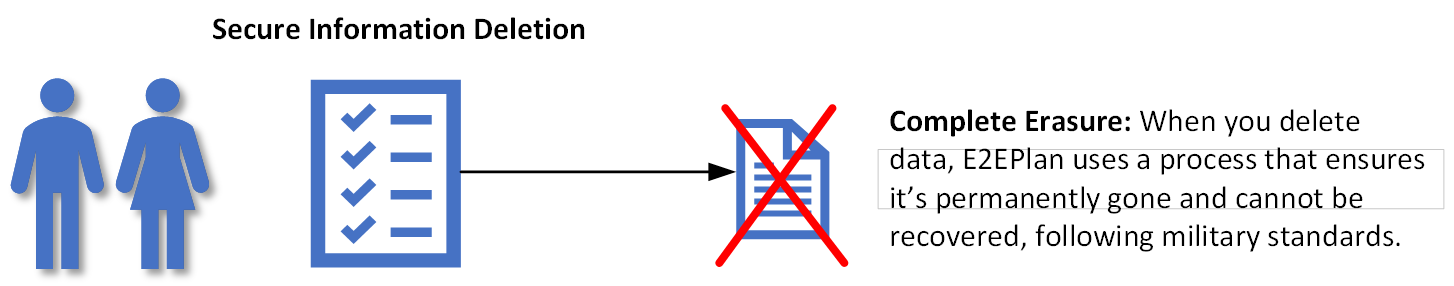
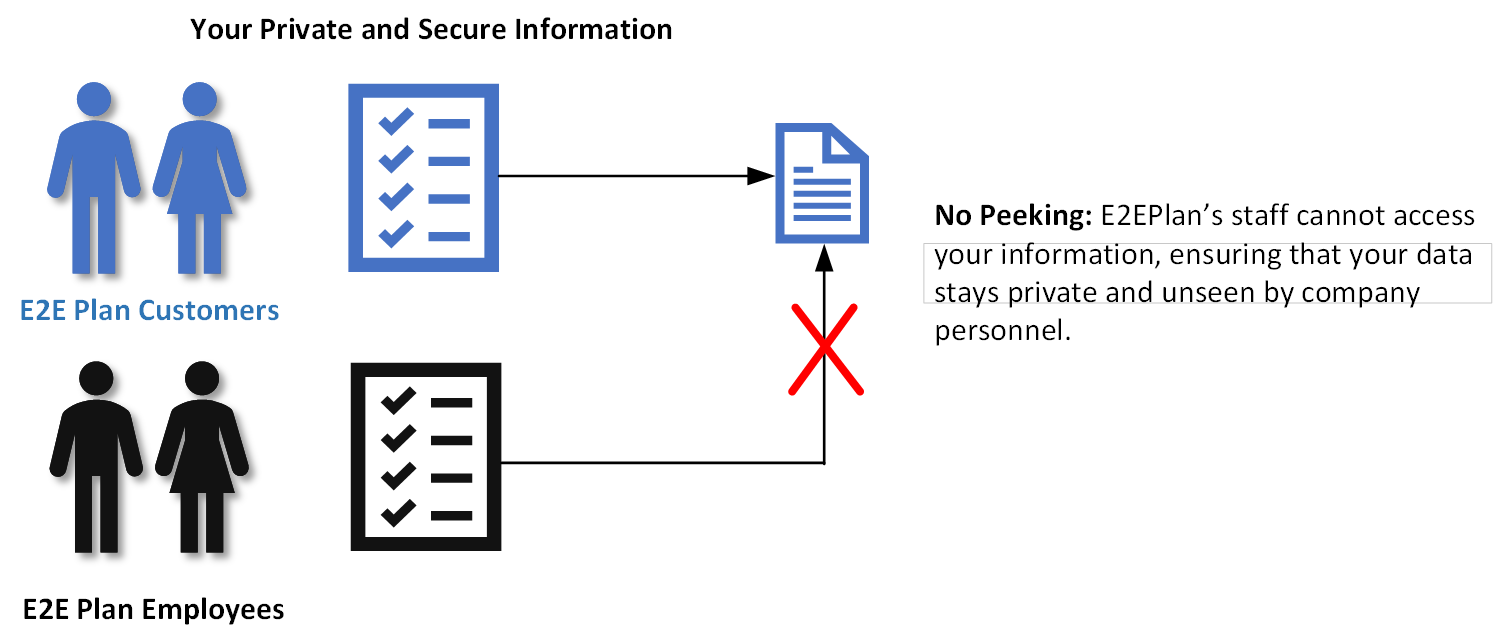
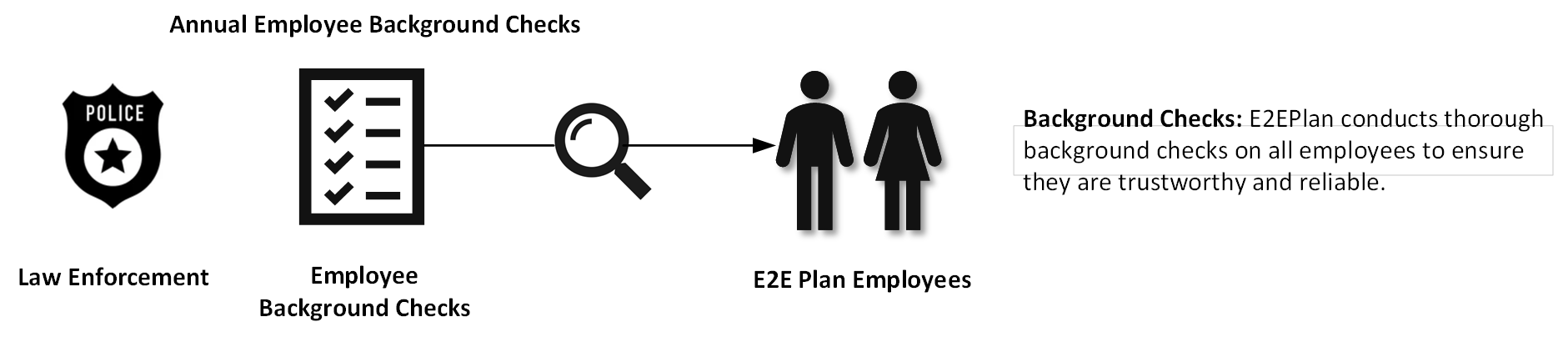
Security Overview
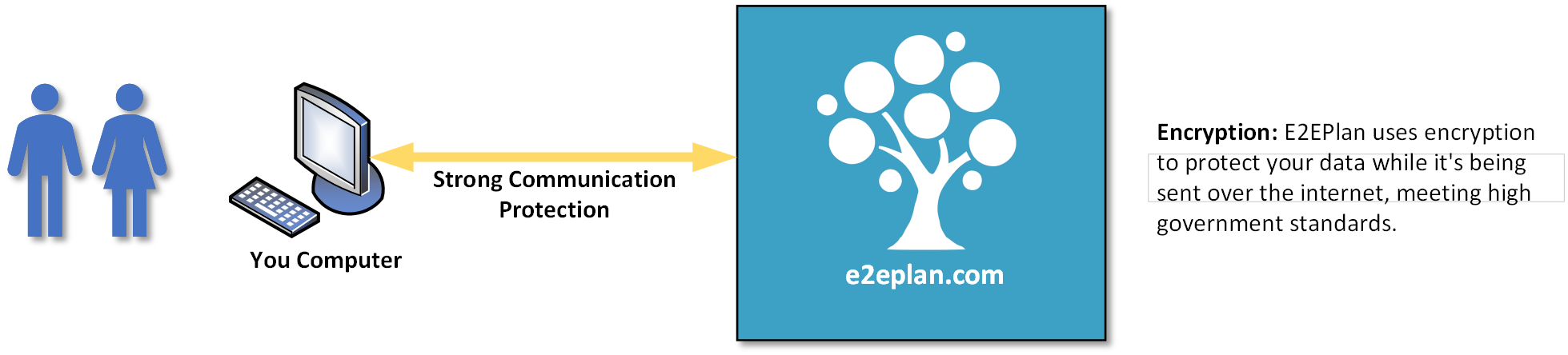
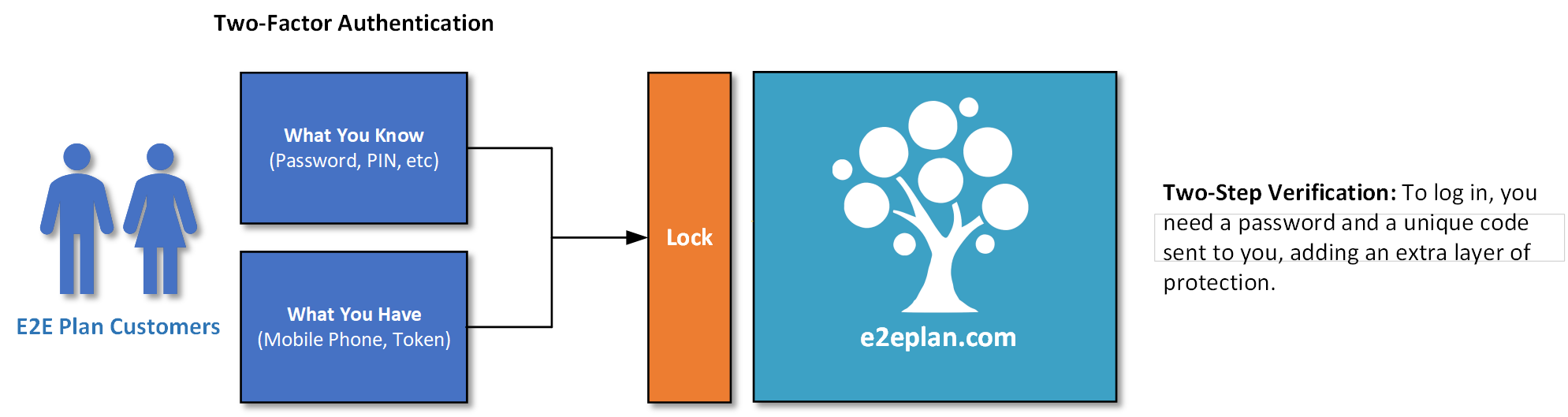
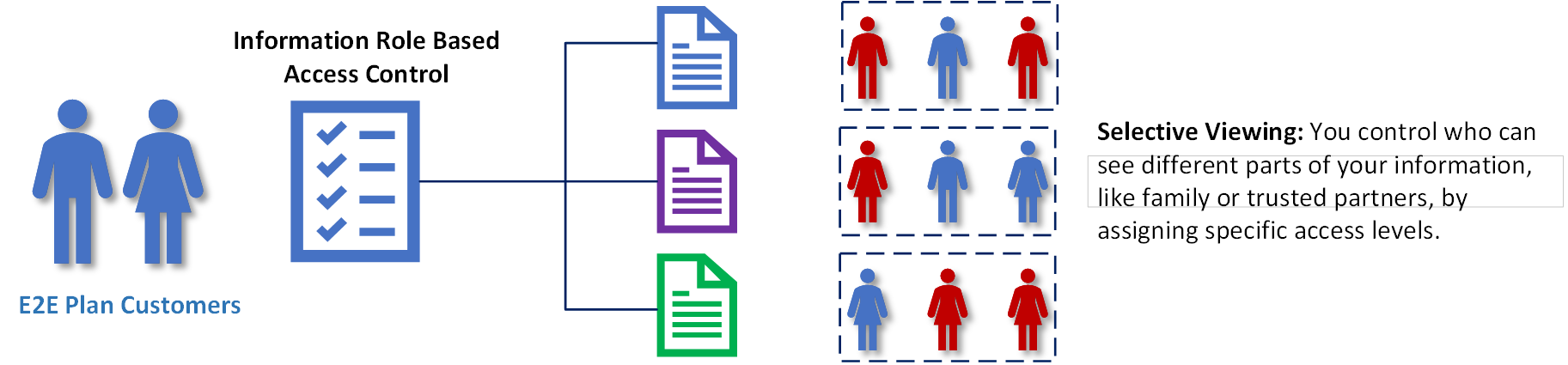
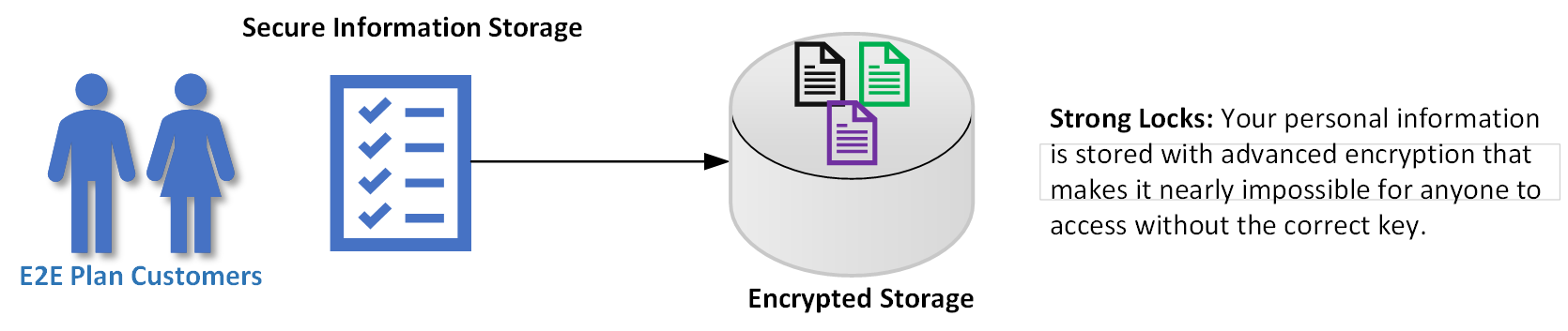
Our first few attempts at explaining our security architecture were, as our friends and family described it, way too technical. Apparently, most users really don’t care that we’re using FIPS 140-2 compliant asymmetric encryption algorithms at the transport layer and FIPS-197 symmetric encryption for data at rest, etc, etc. They just want to know it’s secure and have a high level understanding of how it’s secure.
So we did an infographic for them, kind of as a joke, but they liked it, so here you go. If you'd rather read a snazzy high level overview (pdf) please click here.
1
Create your account
2
Pick your categories
3
Decide who gets access to what & when
4
Gather your data
5
Add it to your plan
6
Relax! Update only as needed
